Mux (multiplex) vlan is Huawei Private vlan. The concept of a private vlan is to provide Layer 2 traffic isolation between ports.
Mux vlan includes three types of ports.
Mux Vlan port - A Mux Vlan is the master Vlan. A Mux Vlan port can communicate with all ports including separate and group ports. Vlans that correspond to the separate and group ports need to be bound to the Mux Vlan.
Subordinate Separate port - separate ports belong to a separe Vlan and can communicate with the Mux Vlan only. Traffic is forward to the related Mux Vlan port.
Subordinate Group port - group ports belong to the group Vlan and can communicate with each other and with the related Mux Vlan ports. Group ports and separate ports do not communicate with each other.
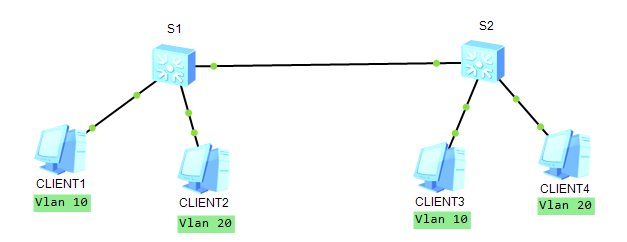
topology:
clients in the subordinate group vlan are able to ping the gateway and each other but they are NOT able to ping clients in the subordinate separate vlan.
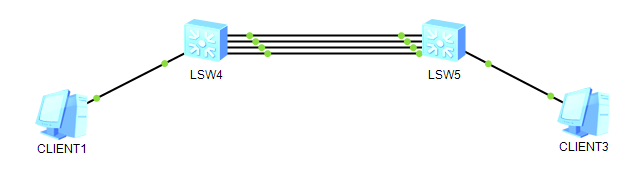
topology:
1 - Configure AR1:
[AR1] interface g0/0/0 [AR1-GigabitEthernet0/0/0] ip address 192.168.0.254 24
2 - Configure S1:
[S1] vlan batch 5 7 10 [S1] vlan 10 [S1-Vlan10] mux-vlan [S1-Vlan10] subordinate separate 5 [S1-Vlan10] subordinate group 7 [S1-Vlan10] quit [S1] interface g0/0/1 [S1-GigabitEthernet0/0/1] port link-type access [S1-GigabitEthernet0/0/1] port default vlan 5 [S1-GigabitEthernet0/0/1] port mux-vlan enable [S1-GigabitEthernet0/0/1] interface g0/0/2 [S1-GigabitEthernet0/0/2] port link-type access [S1-GigabitEthernet0/0/2] port default vlan 5 [S1-GigabitEthernet0/0/2] port mux-vlan enable [S1-GigabitEthernet0/0/2] interface g0/0/3 [S1-GigabitEthernet0/0/3] port link-type access [S1-GigabitEthernet0/0/3] port default vlan 5 [S1-GigabitEthernet0/0/3] port mux-vlan enable [S1-GigabitEthernet0/0/3] interface g0/0/9 [S1-GigabitEthernet0/0/9] port link-type access [S1-GigabitEthernet0/0/9] port default vlan 7 [S1-GigabitEthernet0/0/9] port mux-vlan enable [S1-GigabitEthernet0/0/9] interface g0/0/10 [S1-GigabitEthernet0/0/10] port link-type access [S1-GigabitEthernet0/0/10] port default vlan 7 [S1-GigabitEthernet0/0/10] port mux-vlan enable [S1-GigabitEthernet0/0/10] interface g0/0/24 [S1-GigabitEthernet0/0/24] port link-type access [S1-GigabitEthernet0/0/24] port default vlan 10 [S1-GigabitEthernet0/0/24] port mux-vlan enable
3 - Clients:
Client1 - 192.168.0.1 255.255.255.0 / GW - 192.168.0.254
Client2 - 192.168.0.2 255.255.255.0 / GW - 192.168.0.254
Client3 - 192.168.0.3 255.255.255.0 / GW - 192.168.0.254
Client7 - 192.168.0.7 255.255.255.0 / GW - 192.168.0.254
Client8 - 192.168.0.8 255.255.255.0 / GW - 192.168.0.254
Connectivity test:
clients in the subordinate separate Vlan will NOT be able to ping clients in the subordinate group vlan and each other but will be able to ping the gateway.