GNS3 along with UNL is one of the most used network emulators that allows us to create multi vendor topologies. Unfortunately there are no Huawei images to use within GNS3, but we can connect Huawei eNSp with GNS3 using the cloud.
On Windows 8 you can connect Huawei eNSP to the physical network if on the cloud configurations you select your physical connection, you will then be able to ping the physical address on the host pc and that's all, you will not be able to ping any further then that.
I've seen tutorials on the net whereby configuring the cloud to use your physical connection you can connect Huawei eNSP with GNS3. But on Windows 8 things don't work like that.
So to accomplish this we need to create a loopback adaptor and connect eNSP and GNS3 through the loopback adaptor. If we share the physical connection with the loopback adaptor we will then be able to access the real network.
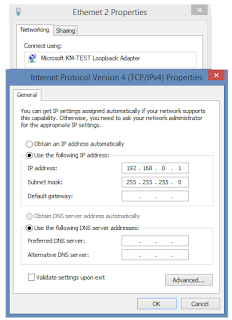
The first step is to create a loopback adaptor which we will not cover here, note that you can assign any ip address to the loopback adaptor. In my loopback adaptor the ip address is 192.168.0.0/24 as you can see from the following picture. It is also important to remember the name of your loopback adaptor, in my case is Ethernet 2.
Next we configure the eNSP, drag and drop a cloud, right-click, select settings and configure as shown in the following picture.
Now we configure GNS3, drag and drop a cloud, right-click, select configure and configure as shown in the following picture.
And we are ready to start pinging each other.